MetaCTF February 2025 Flash CTF consists of 5 challenges.
Cookie Crackdown
We’re auditing some websites to check if they’re GDPR compliant, and I’m pretty sure this site isn’t…
Upon loading the site, we are presented with a modal requiring us to consent to cookies.
From the challenge description and the web page, we can assume that the flag is probably stored as a cookie.
Pressing F12 will bring up the Developer menu. Navigating to the Application tab and then selecting Cookies will reveal a cookie conveniently named flag.
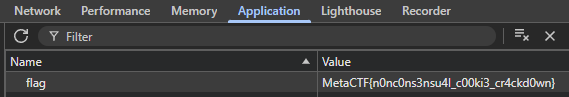
better_eval()
I just want to let people run python code, but they keep trying to read flag.txt. So, I made a better eval that has filters to stop this!
Download the code here and connect to the remote instance with nc [REDACTED] 30019
In the event that remote instance goes down, you can also use nc [REDACTED] 5110. These two are identical, this is just the backup.
Here’s the Python code
#!/usr/local/bin/python
def better_eval(untrusted_code):
blocked_terms = ["flag", "+", "import", "os", "eval", "exec"]
for term in blocked_terms:
if term in untrusted_code:
print(f"The term {term} is filtered!")
return
try:
# Execute the user input in the restricted environment without globals or locals
print(eval(untrusted_code))
except Exception as e:
print(f"Error: {e}")
while True:
untrusted_code = input("Enter your python code> ")
better_eval(untrusted_code)
We can see that there is a list of blocked keywords, including import, os, and flag.
Although this appears to impose strict limitations, we can bypass the filter with a simple one-liner using obfuscation:
print(open("txt.galf"[::-1]).read().strip())
This command opens and prints the content of the flag.txt file. To evade the filter, we spell “flag.txt” backwards and then reverse it in Python to access the correct filename.
Exploiting the filter
└─$ nc [REDACTED] 30019
Enter your python code> print(open("txt.galf"[::-1]).read().strip())
MetaCTF{f1l73rs_d0_n0t_s3cur3_u}
None
Enter your python code>
By reversing the string flag.txt, we successfully bypassed the keyword filter and retrieved the flag. This demonstrates that simple blacklisting of keywords is not a reliable security measure, as it can often be circumvented with obfuscation techniques.
Till Delete Do Us Part
I was messing with trying to dual boot, and while trying to fix partitions, I accidentally deleted the one on my wedding flash drive I carelessly had plugged in! Please help me recover it!
Once we download the file, we need to identify its type with file command:
└─$ file usb.img
usb.img: DOS/MBR boot sector
This indicates that the file is a disk image containing a DOS/MBR boot sector. It could represent a USB drive, hard drive, or partition.
We use fdisk or parted to inspect the partitions:
└─$ fdisk -l usb.img
Disk usb.img: 256 MiB, 268435456 bytes, 524288 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disklabel type: dos
Disk identifier: 0xf4fa0c7e
└─$ parted usb.img
WARNING: You are not superuser. Watch out for permissions.
GNU Parted 3.6
Using /home/kali/metactf_ctf 2025 feb/usbnew/usb.img
Welcome to GNU Parted! Type 'help' to view a list of commands.
(parted) print
Model: (file)
Disk /home/kali/metactf_ctf 2025 feb/usbnew/usb.img: 268MB
Sector size (logical/physical): 512B/512B
Partition Table: msdos
Disk Flags:
Number Start End Size Type File system Flags
No partitions are found. Since they might have been deleted, we attempt to recover them.
We use testdisk to restore the lost partition:
testdisk usb.img
- Select Proceed
- Choose Intel for the partition table
- Select Analyse -> Quick Search
- Locate the FAT32 partition and select Write
- Confirm with
Yand press Enter
If we check again with fdisk or parted, the partitions should be restored:
└─$ fdisk -l usb.img
Disk usb.img: 256 MiB, 268435456 bytes, 524288 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disklabel type: dos
Disk identifier: 0xf4fa0c7e
Device Boot Start End Sectors Size Id Type
usb.img1 * 2048 524287 522240 255M b W95 FAT32
─$ parted usb.img
(parted) print
Model: (file)
Disk /home/kali/metactf_ctf 2025 feb/usbnew/usb.img: 268MB
Sector size (logical/physical): 512B/512B
Partition Table: msdos
Disk Flags:
Number Start End Size Type File system Flags
1 1049kB 268MB 267MB primary fat32 boot
Next, we will need to mount the drive. To mount a disk image containing partitions, we must specify the offset so the system knows where the partition starts. The offset is calculated as:
Offset = Starting Sector × Sector Size
Offset = 2048 × 512 = 1048576
For most disks the sector size is 512.
We can mount the partition:
sudo mount -o loop,offset=1048576 usb.img /mnt/usb
Once mounted, we can explore the drive. Let’s check the Wedding photos directory for any hidden messages:
strings *.jpg | grep -i Meta
Nothing comes up.
We can use also SleuthKit and fls to list all files, including deleted ones:
fls -r -o 2048 usb.img
Nowe we have a list of all the files and directories, including the ones marked as deleted.
d/d 62691: .Meta
+ d/d 62677: CTF
++ d/d 62710: {n
+++ d/d 62725: 0
++++ d/d 62742: t
+++++ d/d 62757: _
++++++ d/d 62774: ev
+++++++ d/d 62790: 3n
++++++++ d/d 62805: _
+++++++++ d/d 62822: d3
++++++++++ d/d 62838: l3t
+++++++++++ d/d 62854: 10n
++++++++++++ d/d 62869: _
+++++++++++++ d/d 62886: c4
++++++++++++++ d/d 62902: n
+++++++++++++++ d/d 62917: _
++++++++++++++++ d/d 62934: s3
+++++++++++++++++ d/d 62950: part
++++++++++++++++++ d/d 62965: 3_
+++++++++++++++++++ d/d 62982: u
++++++++++++++++++++ d/d 62997: 5}
The flag is made of nested directories. Extract the directories’ names to reconstruct it.
Files marked for deletion can be recovered with icat and the sector offset:
icat -o 2048 usb.img 63014 > clue.txt
This extracts clue.txt from sector 63014.
Carrot
Our threat intelligence has found a malware sample that seems heavily targeted at our competitor, MeatCTF. We tried to analyze it, but it just does nothing when we run it in a VM, can you help us analyze this?
Download the sample here and unzip with the password infected
Extract the file and run file:
└─$ file carrot
carrot: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=fd82f7845645aea67dee789f5cac0de456e83108, for GNU/Linux 4.4.0, stripped
This is a 64-bit Linux ELF binary, dynamically linked and PIE-enabled, keep that in mind for later.
Load it into IDA for static analysis. Press F5 to generate pseudocode.
Scrolling through the functions, we find .PEM_read_bio_RSA_PUBKEY, indicating that encryption is likely occurring somewhere in the code.
Open the main function and its pseudocode.
We can see there’s a block of if statements that lead to more code execution. To reach that point in the code, we will need to pass the validation checks presented by the aforementioned if block.
if ( !(unsigned int)sub_3531(a1, a2, a3)
&& !(unsigned int)sub_371A()
&& !(unsigned int)sub_3773()
&& !(unsigned int)sub_356F()
&& !(unsigned int)sub_3622()
&& (unsigned int)sub_37DA()
&& (unsigned int)sub_32B6()
&& !(unsigned int)sub_3378()
&& (unsigned int)sub_3503()
&& !(unsigned int)sub_2C87()
&& (int)sub_2C5A() > 1 )
{
There are quite a few, so let’s go through them.
sub_3531()
This function appears to check if ptrace is running. Since we do not use ptrace, we can ignore this one.
sub_371A()
_BOOL8 sub_371A()
{
time_t v0; // rax
_BOOL8 result; // rax
time_t v2; // rbx
time_t v3; // rdi
double v4; // xmm0_8
v0 = time(0LL);
if ( v0 == -1 )
return 0LL;
v2 = v0;
sleep(0x96u);
v3 = time(0LL);
if ( v3 == -1 )
return 0LL;
v4 = difftime(v3, v2);
result = 1LL;
if ( v4 >= 149.95 )
return v4 > 150.25;
return result;
}
This is an anti-debugging function. It gets the system time, sleeps for 150 seconds, then gets the system time again after sleep. If the difference between the two times is about 150 seconds, it returns true, allowing the check to pass. If the difference is not close to 150 seconds, it returns false, and the check fails.
There are numerous ways to bypass this, but the easiest approach is to change the value of the sleep timer to 1 second (0x1 in hex).
Right click on the instruction, select Manual, and change 96h to 1h
| Address | Original | Patch |
|---|---|---|
| 372C | mov edi, 96h | mov edi, 1h |
Next, go to the main function, select the following instruction, then go to Edit -> Patch Program -> Change Byte:
| Address | Instruction |
|---|---|
| 248C | jnz short loc_2477 |
Replace the opcode for jnz (75) with jz (74) to reverse the if-statement:
74 E9 E8 E0 12 00 00 85 C0 75 E0 E8 D3 10 00 00
| Address | Original | Patched |
|---|---|---|
| 248C | jnz short loc_2477 | jz short loc_2477 |
sub_3773()
Another function that involves timers.
The loop continues until the difference (difftime(v2, v0)) is at least 150.0 seconds.
Once the loop exits, it calculates the final difference (v3 = difftime(v2, v0)) and sets result to 1 (TRUE).
At the end, it checks if v3 is greater than or equal to 149.95. If so, it returns whether v3 is greater than 150.25.
| 0 (false) | 1 (true) |
|---|---|
| If time(0LL) fails (returns -1). | If v3 >= 149.95 and v3 > 150.25. |
| If v3 >= 149.95 but v3 <= 150.25. | If v3 < 149.95. |
do
v2 = time(0LL);
while ( difftime(v2, v0) < 150.0 );
v3 = difftime(v2, v0);
result = 1LL;
if ( v3 >= 149.95 )
return v3 > 150.25;
The validation check only passes if the function returns FALSE. Let’s patch it and reverse the process.
The opcode for ja is 77.
The opcode for jb is 72.
| Address | Original | Patch |
|---|---|---|
| 37A9 | ja short loc_3788 | jb short loc_3788 |
| Address | Original | Patch |
|---|---|---|
| 37C7 | ja short loc_37D6 | jb short loc_37D6 |
Go back to main().
| Address | Original | Patch |
|---|---|---|
| 2495 | jnz short loc_2477 | jz short loc_2477 |
sub_356F()
This checks ensures the code is not running in a VM. Specifically, it opens /proc/cpuinfo and checks whether or not “hypervisor” is present.
Reverse it by patching jnz to jz in main(). Opcodes were provided earlier in the write-up.
| Address | Original | Patch |
|---|---|---|
| 249E | jnz short loc_35BB | jz short loc_35BB |
sub_3622()
Another anti-VM check. This one looks for the strings QEMU, VirtualBox, and VMware.
Just patch it in main().
| Address | Original | Patch |
|---|---|---|
| 24A7 | jnz short loc_2477 | jz short loc_2477 |
sub_37DA()
This function uses curl to open two addresses: https://metactf.com and https://e205e724dda896b5a70bb03b7aed1dba.metactf.com.
If the first address returns HTTP status code 200, v0 is set to TRUE.
After this, curl tries to open the second address, and if the HTTP code is NOT 200, v0 is set to TRUE, and the function returns v0.
For this validation to pass, the first URL needs to be accessible, and the second URL must not be.
If we do a DNS check, we will find out that the second (sub)domain has no DNS records, so we don’t need to do anything here.
sub_32B6()
This function validates the IP address of the machine. It checks if the machine’s IP address starts with 10.13.37.. To bypass this, we will patch it in main().
__int64 sub_32B6()
{
struct ifaddrs *i; // rbx
const struct sockaddr *ifa_addr; // rdi
struct ifaddrs *ifap; // [rsp+8h] [rbp-430h] BYREF
char host[1025]; // [rsp+17h] [rbp-421h] BYREF
unsigned __int64 v5; // [rsp+418h] [rbp-20h]
v5 = __readfsqword(0x28u);
if ( getifaddrs(&ifap) == -1 )
{
LODWORD(i) = 0;
}
else
{
for ( i = ifap; i; i = i->ifa_next )
{
ifa_addr = i->ifa_addr;
if ( ifa_addr
&& ifa_addr->sa_family == 2
&& !getnameinfo(ifa_addr, 0x10u, host, 0x401u, 0LL, 0, 1)
&& !strncmp(host, "10.13.37.", 9uLL) )
{
LODWORD(i) = 1;
break;
}
}
This function fills ifap with a linked list of all network interfaces on the system.
The code iterates through every node in the linked list, extracts and processes interface addresses, uses getnameinfo() to resolve IP addresses into hostnames and then strncmp() to compare the first 9 characters of the host string to the target IP prefix(10.13.37.).
We can patch this in main().
| Address | Original | Patch |
|---|---|---|
| 24BB | jz short loc_2477 | jnz short loc_2477 |
sub_3378()
This function checks running processes. It ensures that processes like Wireshark, Pspy, gdb, strace, or ltrace aren’t running. Additionally, it checks that apache2 is running, as it’s a must requirement to pass the check.
v0 = 0;
v10 = __readfsqword(0x28u);
v1 = opendir("/proc");
if ( v1 )
{
v2 = v1;
v0 = 1;
while ( 1 )
{
v3 = readdir(v2);
if ( !v3 )
break;
if ( v3->d_type == 4 )
{
d_name = v3->d_name;
if ( atoi(v3->d_name) > 0 )
{
snprintf(s, 0x100uLL, "/proc/%s/cmdline", d_name);
v5 = fopen(s, "r");
v6 = v5;
if ( v5 )
{
if ( fgets(haystack, 1024, v5) )
{
if ( strstr(haystack, "wireshark")
|| strstr(haystack, "pspy")
|| strstr(haystack, "gdb")
|| strstr(haystack, "strace")
|| strstr(haystack, "ltrace") )
{
v0 = 1;
fclose(v6);
break;
}
v0 = (strstr(haystack, "apache2") == 0LL) & (unsigned __int8)v0;
}
We can patch this check in main().
| Address | Original | Patch |
|---|---|---|
| 24C6 | jnz short loc_2477 | jz short loc_2477 |
sub_3503()
This function validates the username of the user and it can be patched in main()
| Address | Original | Patch |
|---|---|---|
| 24CF | jz short loc_2477 | jnz short loc_2477 |
sub_2C87()
This function validates the environment variable LD_PRELOAD in the UNIX-like operating systems.
LD_PRELOAD allows to specify shared libraries to be loaded before all others when a program is executed. By doing so, existing functions can be overridden or extended.
We are not doing anything like that and thus this doesn’t need to be patched.
sub_2C5A()
This function performs another anti-VM check, looking at the fan count. Virtual machines typically report a fan count of zero, which would cause the check to fail.
This is done by reading /sys/devices, /sys/class/hwmon, /proc/acpi/fan - virtual filesystems that expose kernel and system information to user space.
The patch for this is applied in main(), where the instruction jle can be changed to jge.
Opcode for JLE is 7E and JGE is 7D
| Address | Original | Patch |
|---|---|---|
| 24E3 | jle short loc_2477 | jge short loc_2477 |
sub_2793()
This function checks the hostname of the machine, expecting it to be www.
To bypass this, we need to patch main().
if ( v3 && (v5 = strcmp(v3, "www")) == 0 )
| Address | Original | Patch |
|---|---|---|
| 2508 | jz short loc_2524 | jnz short loc_2524 |
sub_2C9F()
More checks but we are at the end.
v4 = (char *)sub_2C9F();
char *sub_2C9F()
{
char *v0; // rbx
char *v1; // rbp
char *v2; // r12
char *v3; // r13
__int64 v4; // r15
char *v5; // rax
char *v6; // r14
unsigned int v8; // [rsp+Ch] [rbp-3Ch]
v0 = (char *)sub_2826();
v1 = (char *)sub_2793();
v2 = (char *)sub_27FB();
v3 = (char *)sub_298E();
v4 = (unsigned int)sub_2C5A();
v8 = sub_2C87();
v5 = (char *)malloc(0x2000uLL);
v6 = v5;
if ( v5 )
{
if ( !v3 )
v3 = "unknown";
if ( !v2 )
v2 = "unknown";
if ( !v1 )
v1 = "unknown";
if ( !v0 )
v0 = "unknown";
snprintf(
v5,
0x2000uLL,
"{\"ip_addresses\": \"%s\", \"hostname\": \"%s\", \"username\": \"%s\", \"processes\": \"%s\", \"fan_count\": %d, \""
"ld_preload_set\": %d}",
v0,
v1,
v2,
v3,
v4,
v8);
}
else
{
perror("malloc");
free(v0);
free(v1);
free(v2);
free(v3);
}
return v6;
}
This time, there are four new functions, along with the previous `LD_PRELOAD and fan count checks. The four new functions peform a duplicate functionality of some of the previous validations.
| Function | Validation |
|---|---|
| sub_2826 | IP Address |
| sub_2793 | Hostname |
| sub_27FB | Username |
| sub_298E | Apache2 process |
Earlier, we identified the executable as PIE-enabled. This means the executable uses relative addressing for its functions and data instead of hardcoded absolute memory addresses.
The code references locations relative to the current instruction pointer (RIP). This allows the program to run correctly no matter where it’s loaded in memory.
What does this have to do with the patching? Well, we will apply patches using relative addresses.
Instead of patching the functions, we will patch the if-statements and the unknown strings that are assigned.
Lets start off with v3, which is supposed to return apache2.
How is the relative address calculated?
(address of string)-(address of lea instruction + 7)
7 is the instruction size estimate for lea
Pressing SHIFT+F12 brings up the strings list. There we can find the apache2 string at location 0x41AF. lea instruction is located at 0x2D33
Offset = 41AF - (2D33 + 7) = 1475
= 75 14 converted to Little-Endian
Now that we have the correct offset, we can change the code.
Select the following instruction and patch the code(Edit->Patch Program->Change Bytes). Keep the first 3 bytes and add the offset.
| Address | Original | Patch |
|---|---|---|
| 2D33 | 4C 8D 2D 58 13 00 00 | 4C 8D 2D 75 14 00 00 |
We repeat the same process for v2(meatctf), v1(www) and v0(10.13.37.).
The calculated offsets are as follows:
| Name | Offset (Little-Endian) |
|---|---|
| v2(meatctf) | 71 14 |
| v1(www) | 6B 15 |
| v0(10.13.37.) | 26 14 |
Now that assigned values are patched we need to patch and reverse the if-statements too.
| Address | Original | Patch |
|---|---|---|
| 2D31 | jnz short loc_2D3A | jz short loc_2D3A |
| 2D3D | jnz short loc_2D46 | jz short loc_2D46 |
| 2D49 | jnz short loc_2D52 | jz short loc_2D52 |
| 2D55 | jnz short loc_2D5E | jz short loc_2D5E |
sub_2C87() is the LD_PRELOAD. This one we can ignore again.
sub_2C5A() is the fan check, but instead of patching the function itself, a patch can be applied to sprintf() in sub_2C9F(), which appears to store some kind of JSON data.
| Address | Instruction |
|---|---|
| 2D6E | lea rdx, aIpAddressesSHo |
Double-click on aIpAddressesSHo to go to the string, switch to Hex-View and replace the %d delimeter after fan_count with a number above 0, like 2. Apply the change.
That was all. Save the changes and run the program.
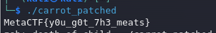
Binary patch
Download carrot.diff
Apply the patch.
bspatch carrot carrot_patched carrot.diff